This .ini file contained all the settings, properties and configuration required for the given executable program to function properly. However, this proved very inefficient due to the redundancy of certain information and it also posed a security threat to the executable program. As a result, a new implementation of standardized, centralized as well as secure technology was an apparent necessity. Double-click any entry in the Windows Defender key/folder to see the value and the options for editing. For example, double-clicking the “IsServiceRunning” DWORD will allow you to edit the value data, in Hexadecimal or Decimal.
- Jet Clean is a good option if you want to scan the entire download api-ms-win-core-localization-l1-2-0.dll link registry within a few seconds and get access to a single-click interface that allows you to clean your system.
- Tried your advice but aparently the files cant be registered.
- See the appendix for transaction log record format details.
- If the file was successfully deleted, no confirmation message should appear.
The registry is a heart and soul of any Windows system. It contains information that controls how your system appears and how it behaves. This causes RegRipper to ‘rip’ the ‘NTUSER.DAT’ file using all available relevant plugins. The result will be stored in the ‘Report File’ along with a ‘Log file’. The log file contains a log of the success/failure of the plugins executed . As an example, we load ‘NTUSER.DAT’ file from our evidence disk , select the ‘ntuser’ profile in RegRipper and ‘rip it’ .
Jv16 PowerTools’ registry Cleaner component includes a slider bar for you to decide how aggressively you want the tool to scan—safe, normal, aggressive, or very aggressive. After the scan, a report shows a list of the categories of errors, from those with the highest to the lowest . The feature is interesting but not terribly valuable, since it doesn’t offer any details about how it’s identifying the problems.
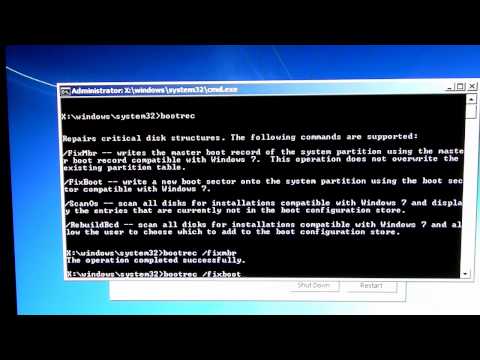
Creating A New Key Or Setting
▪REG_DWORD Represents the data as a four-byte number and is commonly used for Boolean values—for instance, 0 is disabled and 1 is enabled. The data is displayed as a 32-bit (four-byte) long hexadecimal number. States which user was logged into Windows® when a specific USB device was connected. For a list of previously connected USB devices on an author machine. Choose a safe location on your hard drive or external hard drive and save the registries there. Look for the registries of the application that you want to change.
Dll Files?
Instead, use a free registry cleaner if you want to clear out common registry junk automatically. You can now make whatever changes you need to make to the registry, which probably shouldn’t be done unless you’re versed in how to safely add, change, or delete registry keys and values. Make sure, whatever you do, that you only affect the narrow registry areas that you intend to. Control Panel contains settings for the Control Panel, Run contains settings that cause programs to run at startup, Uninstall will contain the uninstallation strings for most programs, etc. The next time you make a settings change you’ll have a better idea of what is going on behind the scenes.
While it is not stored directly on disk, it is neither a simple pointer to another key. Instead it merges the user level component information stored in HKEY_USER\current_user_sid_CLASSES and the system level information in HKLM\Software\Classes. If a key occurs in both places, the user-level value takes precedence. With a large amount of data stored in a configuration the speed of creating such a config in registry becomes an issue. Any application that does not uninstall properly, or does not have an uninstaller, can leave entries in the registry.
In Windows, use of the registry for storing program data is a matter of developer’s discretion. Microsoft provides programming interfaces for storing data in XML files or database files which developers can use instead. Developers are also free to use non-Microsoft alternatives or develop their own proprietary data stores. The /s means the file will be silent merged to the registry.